There are three main kinds of browser isolation: remote (or cloud-hosted), on-premise, and client-side.There are three basic types of browser isolation technology:
Remote browser isolation runs in a cloud-hosted sandbox—an isolated testing environment—separate from an organization’s internal environment.
On-premises browser isolation works just like RBI, but it’s hosted as part of an organization’s internal IT environment.
Client-side/local browser isolation runs on a user’s endpoint in a virtualized sandbox and wipes browsing data after sessions.
Why is Browser Isolation important?
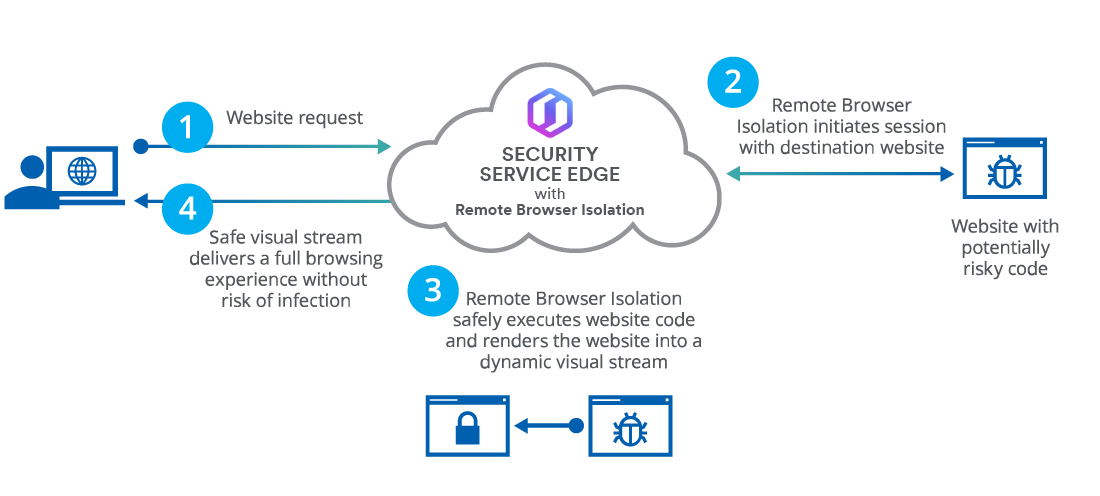
The Need for Isolated Browsing While most website code is legitimate, websites can also contain malicious code designed to steal user credentials or deliver malware to the user’s computer. Browser isolation can protect Internet users’ computers from being infected by malware delivered via the Internet.
Which policy is used in Browser Isolation?
Cloudflare Browser Isolation complements the Secure Web Gateway and Zero Trust Network Access solutions by executing active webpage content in a secure isolated browser. Executing active content remotely from the endpoint protects users from zero-day attacks and malware.
What is isolation in security?
Security isolation relates to the principles of least privilege and privilege separation [Saltzer and Schroeder 1975]. Security isolation is commonly used in two broad ways, depending on the threat model. First, it can be used to safely execute a program that is not trusted or not yet trusted.
What is content isolation?
Content isolation provides context, allowing organizations to easily define controls that prevent isolated content from accessing privileges or launching payloads without limiting the normal user activity.
What is web browser isolation?
Browser isolation protects users from untrusted, potentially malicious websites and apps by confining browsing activity to a secured environment that is separated from user devices and organizational networks. Access Glossary.
What is true about browser isolation?
True browser isolation contains all web activity within a closed virtualized environment without allowing any browser-based code to access other sections of the user’s device. A virtualized browser strategy is far more secure than traditional methods of web access.
What is site isolation in Chrome?
When you turn on site isolation, Chrome offers more security protections for your browser. Chrome will load each website in its own process. So, even if a site bypasses the same-origin policy, the extra security will help stop the site from stealing your data from another website.
How is remote Browser Isolation implemented?
Remote browser isolation is a limited-availability feature and may not be enabled for your account. Use the Web > Settings > Remote Browser Isolation page to enable and configure the feature.
What is an isolated environment?
What is isolation application?
Application Isolation is a network security approach that adds Zero Trust Network Access (ZTNA) controls to Virtual Private Networks (VPNs) and Next Generation Firewalls (NGFWs). This prevents hackers and malicious insiders from gaining unauthorized access to applications and data.
What is isolated application?
Application isolation is the separation of one program or application stack from the rest of the running processes. The oldest way to do this is to simply run your application on a separate computer, but that gets very expensive very quickly.
What is application isolation and containment?
Application containment is used to block harmful file and memory actions to other apps and the endpoint. Application isolation is used to prevent other endpoint processes from altering or stealing from an isolated app or resources.
What is RBI remote Browser Isolation?
Remote browser isolation (RBI), also known as web isolation, is a security measure that separates users’ devices from the act of internet browsing by hosting and running all browsing activity in a remote cloud-based container.
What is Symantec web isolation?
Symantec Web Isolation policies can be configured to send traffic from uncategorized sites and sites with potentially unsafe risk profiles down a Web Isolation path, allowing users access to these sites while helping to ensure the enterprise is protected from any threats these sites pose to the business.
What is Browser Isolation mimecast?
Mimecast Browser Isolation allows users to safely click on any URL embedded in an email or surf to any website, protecting from phishing attempts and malware infections.
Why is it important to isolate this application or service?
Application Isolation is a network security approach that adds Zero Trust Network Access (ZTNA) controls to Virtual Private Networks (VPNs) and Next Generation Firewalls (NGFWs). This prevents hackers and malicious insiders from gaining unauthorized access to applications and data.
What’s the difference between Browser Isolation and remote Browser Isolation?
Remote browser isolation runs in a cloud-hosted sandbox—an isolated testing environment—separate from an organization’s internal environment. On-premises browser isolation works just like RBI, but it’s hosted as part of an organization’s internal IT environment.
What is site isolation in Chrome?
When you turn on site isolation, Chrome offers more security protections for your browser. Chrome will load each website in its own process. So, even if a site bypasses the same-origin policy, the extra security will help stop the site from stealing your data from another website.
What is zscaler Browser Isolation?
Zscaler Cloud Browser Isolation provides a completely safe web experience: Assume the internet is untrusted: Protect against sensitive data theft and stop ransomware, zero-day vulnerabilities, and advanced attacks with an unbreakable air gap between users and destinations.
How do I get out of URL isolation?
If the link is determined to be safe, an option to “exit” isolation will be presented in the upper right hand corner of the screen. Exiting isolation must be clicked on to complete downloads or uploads.
What is remote Browser Isolation Forcepoint?
Remote Browser Isolation (RBI) enforces Zero Trust security for web browsing. Other web security technologies rely on first being able to detect malware, and then respond by blocking malicious content. In contrast, RBI applies a Zero Trust approach by treating all web pages as compromised from the outset. Product Demo.
What is browser isolation cybersecurity and how does it work?
The browser isolation cybersecurity model recognizes that the vast majority of cyberattacks begin with the browser and seeks to physically isolate the browser, along with all of the associated cyber risks, onto a platform that is built to handle those cyber risks while physically isolating them away from your IT infrastructure.
What is client-side browser isolation?
Client-side browser isolation still loads the webpages on a user device, but it uses virtualization or sandboxing to keep website code and content separate from the rest of the device.
What is on-premise browser isolation?
On-premise browser isolation does the same thing, but on a server that an organization manages internally. Client-side browser isolation still loads the webpages on a user device, but it uses virtualization or sandboxing to keep website code and content separate from the rest of the device.
What is remote or cloud-hosted browser isolation?
Remote or cloud-hosted browser isolation keeps untrusted browser activity as far away as possible from user devices and corporate networks. It does so by conducting a user’s web browsing activities on a cloud server controlled by a cloud vendor.