Posts By DIY
-

 562Macbook
562MacbookCan someone put a listening device on my phone?
Mobile phones themselves can be used as bugging devices. They can be programmed not to vibrate, ring or show any outward signs...
-

 575Iphone
575IphoneCan someone hack iPhone texts?
Experts say that just receiving an iMessage from a hacker using this exploit can be enough to leave users’ personal data exposed....
-

 601Iphone
601IphoneCan spyware be installed on iPhone remotely?
Spyware can be loaded onto your iPhone remotely via a malicious app, or physically if someone gains access to your phone. Use...
-
 533Iphone
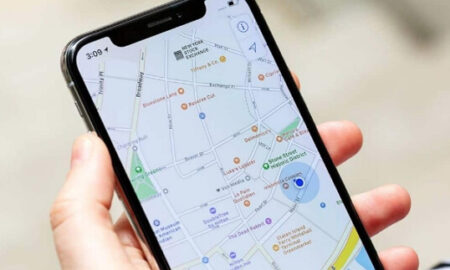
533IphoneHow can I monitor someones iPhone without them knowing?
Use iCloud to Track iPhone Location without Person Knowing The easiest way to monitor someone else’s iPhone is through iCloud. Although you...
-
 620Iphone
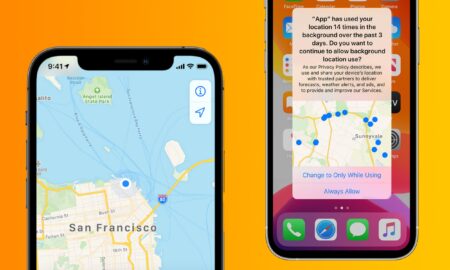
620IphoneCan anyone see my iPhone screen?
Everyone can see what’s on your screen until you stop sharing, but they can’t control anything on your device. If you get...
-
 546Iphone
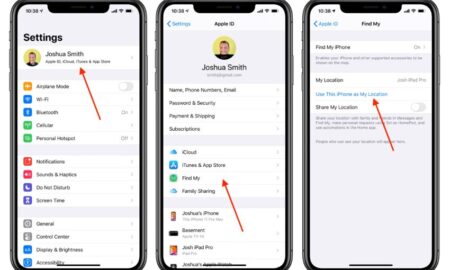
546IphoneCan someone have access to my iPhone without me knowing?
If your iPhone backs everything up to your iCloud account, then someone can spy on your activity by accessing your iCloud account...
-
 519Iphone
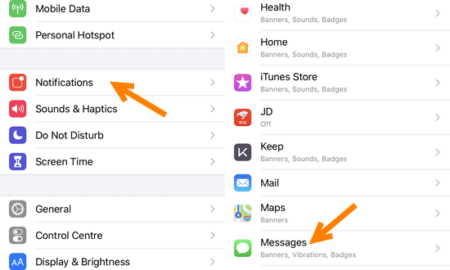
519IphoneHow do you hide messages on iPhone without deleting?
You can hide messages on your iPhone by using message filtering. You can also hide a specific message chain by hiding alerts...
-
 541Iphone
541IphoneCan someone see everything I do on my iPhone?
If your iPhone backs everything up to your iCloud account, then someone can spy on your activity by accessing your iCloud account...
-

 556Iphone
556IphoneCan someone spy on my iPhone without touching it?
Can iPhone spying software be installed remotely? Hackers don’t need to be physically present to sneak spyware onto your phone — it...
-

 532College
532CollegeHow cheaters hide their tracks?
Like hiding their communications with app-hiders or photo lockers, cheaters will also use incognito browser windows to cover their tracks. The browsers...

Recent Comments