Suspicious activity monitoring is a feature included in Malwarebytes Endpoint Detection and Response. It watches for potentially malicious behavior by monitoring the processes, registry, file system, and network activity on the endpoint.
What is suspicious activity on Activity Monitor?
Suspicious activity monitoring is the procedure of identifying, researching, documenting—and, if necessary, reporting—a customer’s banking pattern when it indicates possible illegal behavior. This practice is done to both manage a bank’s risk and comply with regulations.
How can you tell if a Mac is a suspicious process?
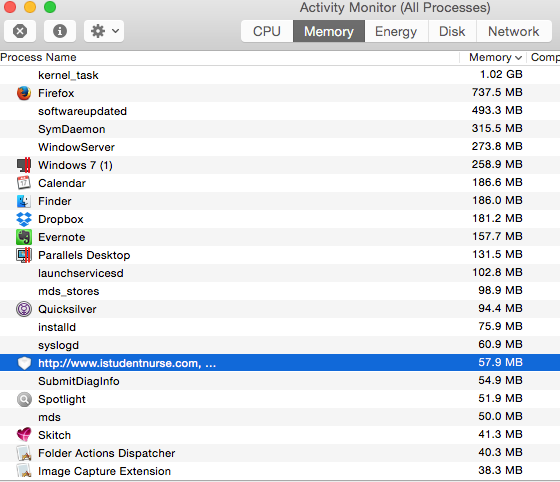
Look for any suspicious processes that are running on your Mac. On the menu bar, click Go, and then select Utilities. Double-click Activity Monitor. Review the list for any processes that look suspicious to investigate further.
What is suspicious activity on Activity Monitor?
Suspicious activity monitoring is the procedure of identifying, researching, documenting—and, if necessary, reporting—a customer’s banking pattern when it indicates possible illegal behavior. This practice is done to both manage a bank’s risk and comply with regulations.
How can you tell if a Mac is a suspicious process?
Look for any suspicious processes that are running on your Mac. On the menu bar, click Go, and then select Utilities. Double-click Activity Monitor. Review the list for any processes that look suspicious to investigate further.
What triggers suspicious activity report?
If potential money laundering or violations of the BSA are detected, a report is required. Computer hacking and customers operating an unlicensed money services business also trigger an action. Once potential criminal activity is detected, the SAR must be filed within 30 days.
What are suspicious transactions?
Any transaction or dealing which raises in the mind of a person involved, any concerns or indicators that such a transaction or dealing may be related to money laundering or terrorist financing or other unlawful activity.
Is the Apple security warning real?
While the message might seem convincing, it’s merely a scam that’s designed to swindle money from unsuspecting users, steal personal data, and spread malware. It’s important to mention that Apple doesn’t send security warnings and this alert is fake.
Is my computer being monitored Mac?
Mac users: Follow these steps To open the Activity Monitor, hit Command + Spacebar to open Spotlight Search. Then, type Activity Monitor and press Enter. Check over the list for anything you don’t recognize. To close out a program or process, double click, then hit Quit.
Can Mac computers be hacked?
Are Macs Hacked? Yes, though not as frequently Windows PCs are, there still have been incidents of hackers compromising Macs. Such hacking can be various, from fake programs to vulnerability exploits. We give you a rundown on the more common forms of malware that are used to hack Macs.
Can Trojan virus be removed from Mac?
You can quickly scan your Mac and remove trojan virus and other malware using the CleanMyMac X menu. It also lets you monitor your Mac performance and manage memory and CPU load.
Does Mac have a built in virus scanner?
How do I prevent someone from accessing my Mac remotely?
Disabling Remote Access for macOS 1. Click the Apple icon > System Preferences, then click the Sharing icon. 2. Uncheck the boxes next to Remote Login and Remote Management.
How do you monitor suspicious transactions?
Companies can detect suspicious financial activities using AML Transaction Monitoring and write a SAR to report the activity to local regulators such as Financial Crimes Enforcement Network (FinCEN) and global regulators such as Financial Action Task Force (FATF).
Is used to monitor for suspicious activity on a network?
An intrusion detection system (IDS) is a system that monitors network traffic for suspicious activity and alerts when such activity is discovered.
What is Hidd on my Mac?
What is hidd? Hidd is an abbreviation of human interface device daemon. In simplest terms, it’s the process that allows your Mac’s mouse or trackpad and keyboard to work. It interprets keyboard commands, mouse movements, and trackpad gestures and passes the results to the relevant part of the OS.
What is MDNSResponder on my Mac?
MDNSResponder, also known as Bonjour, is Apple’s native zero-configuration networking process for Mac that was ported over to Windows and associated with MDNSNSP. DLL. On a Mac or iOS device, this program is used for networking nearly everything.
What is suspicious activity on Activity Monitor?
Suspicious activity monitoring is the procedure of identifying, researching, documenting—and, if necessary, reporting—a customer’s banking pattern when it indicates possible illegal behavior. This practice is done to both manage a bank’s risk and comply with regulations.
How can you tell if a Mac is a suspicious process?
Look for any suspicious processes that are running on your Mac. On the menu bar, click Go, and then select Utilities. Double-click Activity Monitor. Review the list for any processes that look suspicious to investigate further.
How do you identify suspicious transactions?
An assessment of suspicion should be based on a reasonable evaluation of relevant factors, including the knowledge of the customer’s business, whether the transactions are in keeping with normal industry practices, financial history, background and behaviour.
What happens when a suspicious activity report is filed?
The goal of the SAR and the resulting investigation is to identify customers who are involved in money laundering, fraud, or terrorist funding. Disclosure to the customer, or failure to file a SAR, can result in very severe penalties for both individuals and institutions.
What is an example of a suspicious transaction?
transactions that don’t match the customer profile. high volumes of transactions being made in a short period of time. depositing large amounts of cash into company accounts. depositing multiple cheques into one bank account.