Latest News
-

 429Passwords
429PasswordsWhat are the threats to DNS server?
For example, DNS tunneling techniques enable threat actors to compromise network connectivity and gain remote access to a targeted server. Other forms...
-
 483Synonym
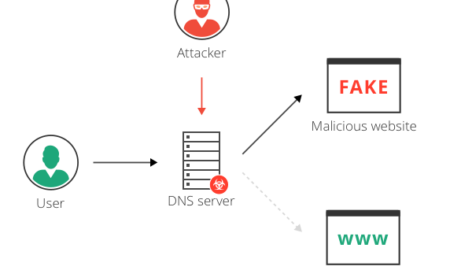
483SynonymHow do hackers attack DNS?
There are different methods of hijacking the DNS, such as poisoning the DNS cache with an incorrect IP address, infiltrating malware into...
-
 408iPhone
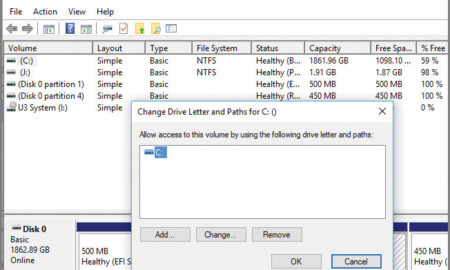
408iPhoneHow do I change my local disk from D to E?
Open Computer Management by selecting the Start button. The select Control Panel > System and Security > Administrative Tools, and then double-click...
-
 462iPhone
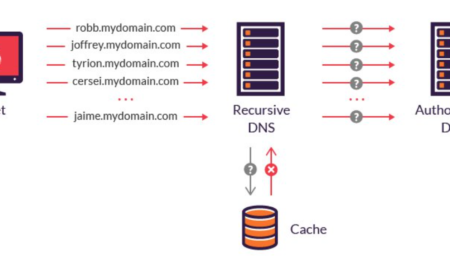
462iPhoneHow DNS can be attacked?
The attacker corrupts a DNS server by replacing a legitimate IP address in the server’s cache with that of a rogue address...
-
 509Apple
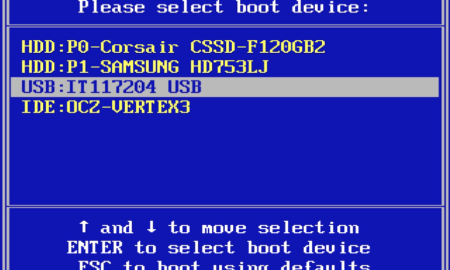
509AppleHow do I choose which drive to boot from outside BIOS?
Restart your computer and you may see a screen that says, “Press F12 Boot for boot Menu” or “Press Del for Setup”....
-

 545Reboot
545RebootCan you change boot order from CMD?
Move Specific Boot Entry As First Entry Open an elevated command prompt. Run bcdedit without parameters to find the {identifier} for the...
-
 439Pros
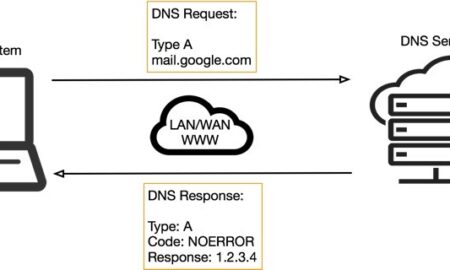
439ProsWhat is malicious DNS traffic?
For instance, DNS is commonly used by malware for discovering C&C (Command and Control) infrastructure, while spammers rely on DNS to redirect...
-
 396Pros
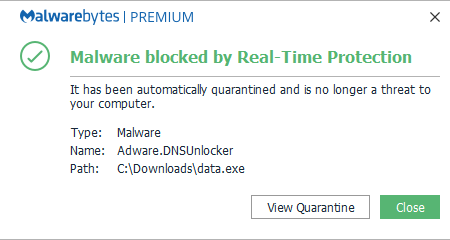
396ProsWhat is Adware DNS?
DNS Unlocker is an adware program that takes over your internet browser with unwanted ads. Its main purpose is for cybercriminals to...
-
 403Ring
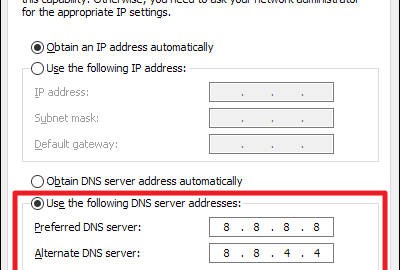
403RingIs Google DNS server safe?
Google Public DNS complies with Google’s main privacy policy, available at our Privacy Center. Your client IP address is only logged temporarily...
-
 475Tf
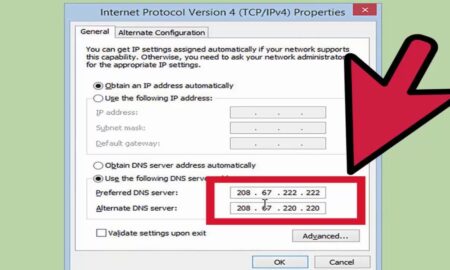
475TfHow do I fix a constant DNS problem?
You can fix a “DNS Server Not Responding” error by resetting your internet connection and computer. If the error keeps appearing, you...
