Latest News
-

 419Software
419SoftwareWhat can someone do with my DNS?
DNS hijacking can be used for pharming (in this context, attackers typically display unwanted ads to generate revenue) or for phishing (displaying...
-
 466Average
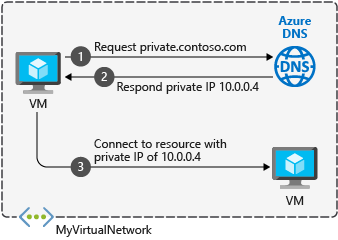
466AverageIs DNS private or public?
Is DNS data public? For a server to be accessible on the public internet, it needs a public DNS record, and its...
-
 503Laptop
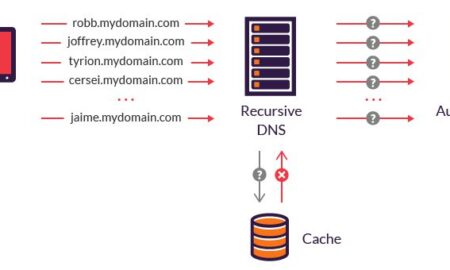
503LaptopWhat are the possible attacks on DNS?
For example, DNS tunneling techniques enable threat actors to compromise network connectivity and gain remote access to a targeted server. Other forms...
-
 545Radar
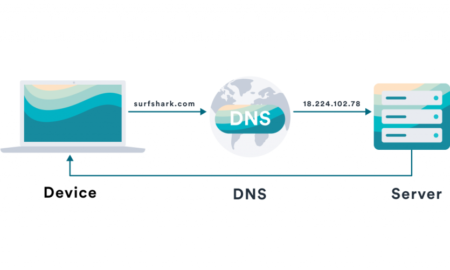
545RadarDoes a VPN hide DNS?
A “Full-Tunnel” VPN routes and encrypts all the Internet traffic through the VPN. Consequently, DNS requests are also encrypted and out of...
-
 433Macs
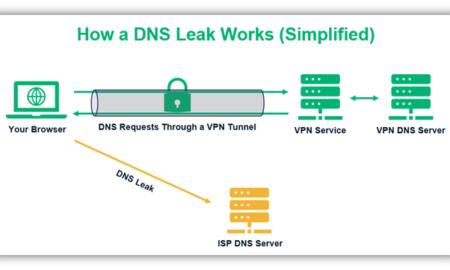
433MacsWhat happens if your DNS is leaked?
What Does a DNS Leak Mean in Terms of Privacy and Security? So, a DNS leak means that someone can intercept the...
-
 455Sound
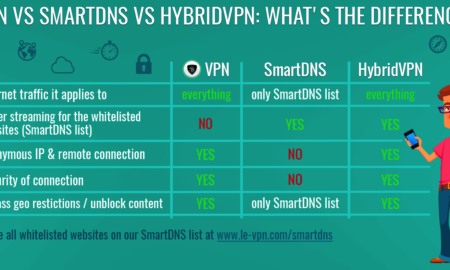
455SoundWhich is safer DNS or VPN?
The main one, being that a VPN is far more secure. That said, if you’re only streaming TV and movie content, Smart...
-
 445Pros
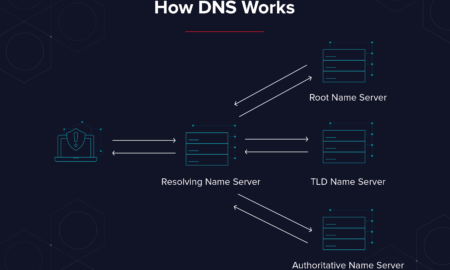
445ProsIs DNS confidential?
Unfortunately, the DNS does not inherently employ any mechanisms to provide confidentiality for these transactions, and the corresponding information can therefore easily...
-
 488Computer
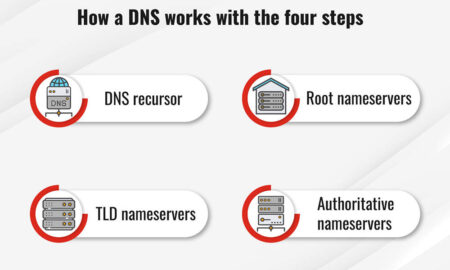
488ComputerCan you be tracked by DNS?
DNS monitoring can also discover and track IP addresses of DNS requests and log every website viewed by a device connected to...
-

 456Windows
456WindowsIs DNS safer than https?
Standard DNS vs DNS over HTTPS Being a superior protocol, a DoH enabled setting offers better prevention from man-in-the-middle attacks. Once enabled,...
-

 432Android
432AndroidWhich is better ATA or AHCI?
If you have SATA drives, use AHCI. ATA runs the SATA controller in compatibility mode and loses the native features. The only...
