Can Google DNS be hacked?
Hackers create malware programs that can change your DNS server settings. For example, if your computer uses Google’s DNS servers and you want to go to your bank’s website, you type in the URL of your bank and expect to be taken to your bank’s official website.
Can DNS be spoofed?
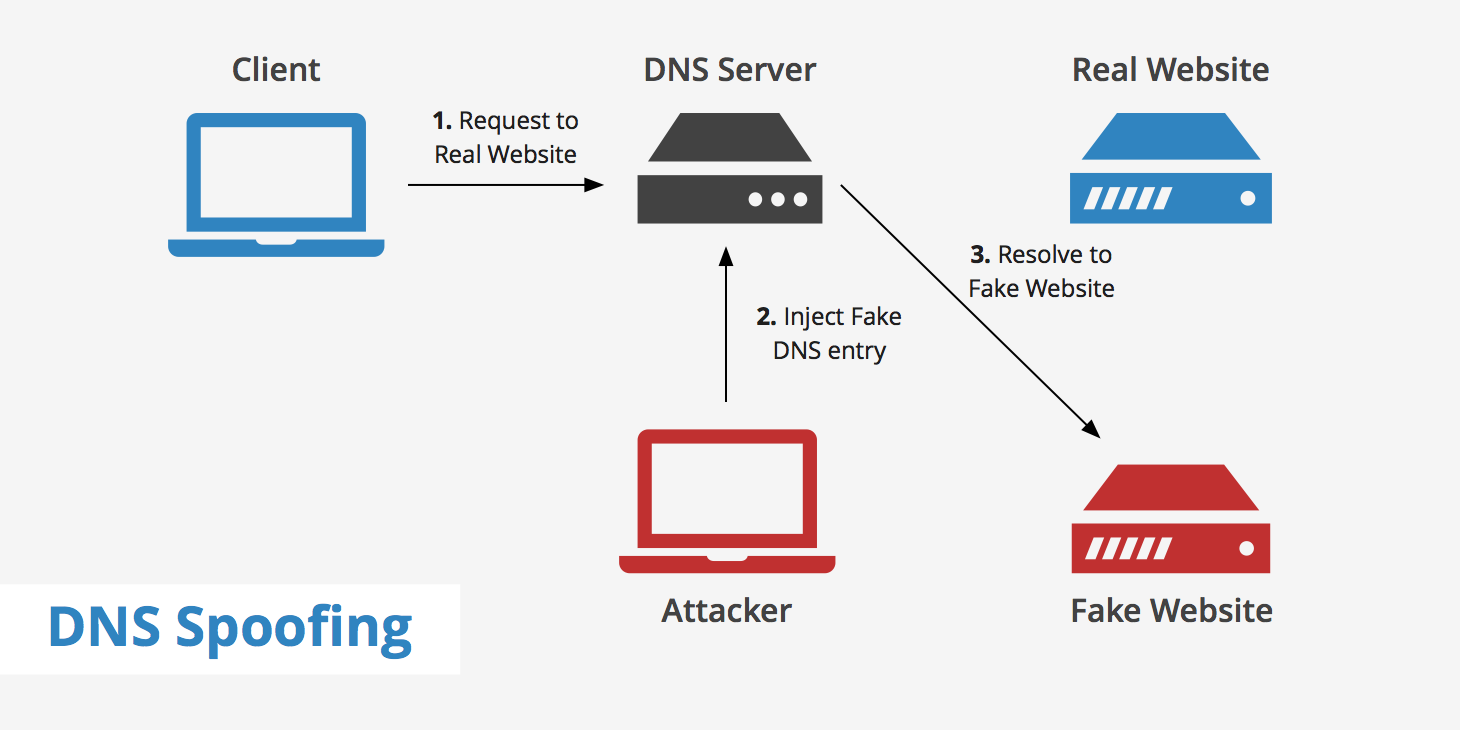
Domain Name Server (DNS) spoofing (a.k.a. DNS cache poisoning) is an attack in which altered DNS records are used to redirect online traffic to a fraudulent website that resembles its intended destination.
How secure is Google DNS?
Google Public DNS offers support for encrypted transport protocols, DNS over HTTPS and DNS over TLS. These protocols prevent tampering, eavesdropping and spoofing, greatly enhancing privacy and security between a client and Google Public DNS. They complement DNSSEC to provide end-to-end authenticated DNS lookups.
How do I know if my DNS is poisoned?
So how do you detect a DNS cache poisoning attack? Monitor your DNS servers for indicators of possible attacks. Humans don’t have the computing power to keep up with the amount of DNS requests you will need to monitor. Apply data security analytics to your DNS monitoring to discern normal DNS behavior from attacks.
How secure is Google DNS?
Google Public DNS offers support for encrypted transport protocols, DNS over HTTPS and DNS over TLS. These protocols prevent tampering, eavesdropping and spoofing, greatly enhancing privacy and security between a client and Google Public DNS. They complement DNSSEC to provide end-to-end authenticated DNS lookups.
Does Google DNS hide IP address?
By default, you probably use DNS servers operated by your Internet Service Provider (ISP) or Google, which can see your IP address when you request a website, even when connected to a VPN.
Can someone hack you through DNS?
A DNS name server is a highly sensitive infrastructure which requires strong security measures, as it can be hijacked and used by hackers to mount DDoS attacks on others: Watch for resolvers on your network — unneeded DNS resolvers should be shut down.
How common is DNS spoofing?
Through their research they discovered that DNS spoofing is still rare (occurring only in about 1.7% of observations) but has been increasing during the observed period, and that proxying is the most common DNS spoofing mechanism.
How do I know if I got spoofed?
If you get calls from people saying your number is showing up on their caller ID, it’s likely that your number has been spoofed. We suggest first that you do not answer any calls from unknown numbers, but if you do, explain that your telephone number is being spoofed and that you did not actually make any calls.
Can VPN prevent DNS spoofing?
Instead of connecting your devices to your internet provider’s local server, a VPN connects to private DNS servers around the world that use end-to-end encrypted requests. This prevents attackers from intercepting traffic and connects you to DNS servers that are better protected from DNS spoofing.
Is Google DNS like VPN?
Our Verdict. Smart DNS and VPN services both unblock geo-restricted websites and stream video content from abroad. However, only a VPN hides your IP address and encrypts your web traffic. Custom DNS doesn’t spoof your location or encrypt your data transfers, but it can improve your internet speeds and security.
Should I use my ISP DNS or Google?
Third-Party DNS Servers Might Be Faster, Too In addition to privacy concerns, DNS services provided by ISPs can be slower than Google or Cloudflare. This isn’t always the case, as your ISP will generally be closer to you than a third party, but many people get faster speeds with a third-party DNS server.
Is it good to use 8.8 8.8 DNS?
That is not recommended and may even be a violation of your security policies, depending on the level of security required in your organization or by any governing agency. DNS forwarders that only point to 8.8. 8.8 are using your ISP connection to hop to 8.8. 8.8 when resolving DNS.
What are the dangers of DNS?
DNS cache poisoning, also known as DNS spoofing, is a cyber-attack that exploits the weaknesses in the Domain Name System (DNS) servers. It enables the attacker to poison the data in DNS servers, including your company server, by providing false information to your internet traffic and diverting it to fake servers.
Can DNS steal your information?
Local DNS hijack Attackers start by installing malware on a user’s computer. The attacker can then change your DNS settings and redirect you to malicious websites, usually to steal your personal data.
What causes DNS spoofing?
Specifically, hackers gain access to a DNS server so that they can adjust its directory to point the domain name users enter to a different, incorrect IP address. Once someone gains access to a DNS server and begins redirecting traffic, they are engaging in DNS spoofing.
What does DNS spoofing do?
DNS (Domain Name Service) spoofing is the process of poisoning entries on a DNS server to redirect a targeted user to a malicious website under attacker control.
What are 4 types of spoofing attacks?
Spoofing can take many forms, such as spoofed emails, IP spoofing, DNS Spoofing, GPS spoofing, website spoofing, and spoofed calls.
What are the dangers of DNS spoofing?
When your DNS server is compromised, many things can go wrong. One of those is redirecting incoming traffic to an illegitimate server where they can launch a series of attacks, including collecting traffic logs that contain sensitive data. Another will allow attackers to capture all inbound emails to your organization.
How secure is Google DNS?
Google Public DNS offers support for encrypted transport protocols, DNS over HTTPS and DNS over TLS. These protocols prevent tampering, eavesdropping and spoofing, greatly enhancing privacy and security between a client and Google Public DNS. They complement DNSSEC to provide end-to-end authenticated DNS lookups.
How do I know if my DNS is poisoned?
So how do you detect a DNS cache poisoning attack? Monitor your DNS servers for indicators of possible attacks. Humans don’t have the computing power to keep up with the amount of DNS requests you will need to monitor. Apply data security analytics to your DNS monitoring to discern normal DNS behavior from attacks.