A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
What is a DDoS attack Cloudflare?
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
What DDoS attack means?
Distributed denial of service (DDoS) attacks are a subclass of denial of service (DoS) attacks. A DDoS attack involves multiple connected online devices, collectively known as a botnet, which are used to overwhelm a target website with fake traffic.
What happens during a DDoS attack?
In a DDoS attack, cybercriminals take advantage of normal behavior that occurs between network devices and servers, often targeting the networking devices that establish a connection to the internet. Therefore, attackers focus on the edge network devices (e.g., routers, switches), rather than individual servers.
What is a DDoS attack Cloudflare?
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
Why do people do DDoS attacks?
The objective of a DDoS attack is typically to harm a company by taking its most essential resources offline. Kaspersky points out that some organizations make especially attractive targets for these types of digital intrusions.
Is DDoS attack hard?
These attacks are also extremely difficult to defend against because of their distributed nature. It is difficult to differentiate legitimate Web traffic from requests that are part of the DDoS attack. There are some countermeasures you can take to help prevent a successful DDoS attack.
How do you detect a DDoS attack?
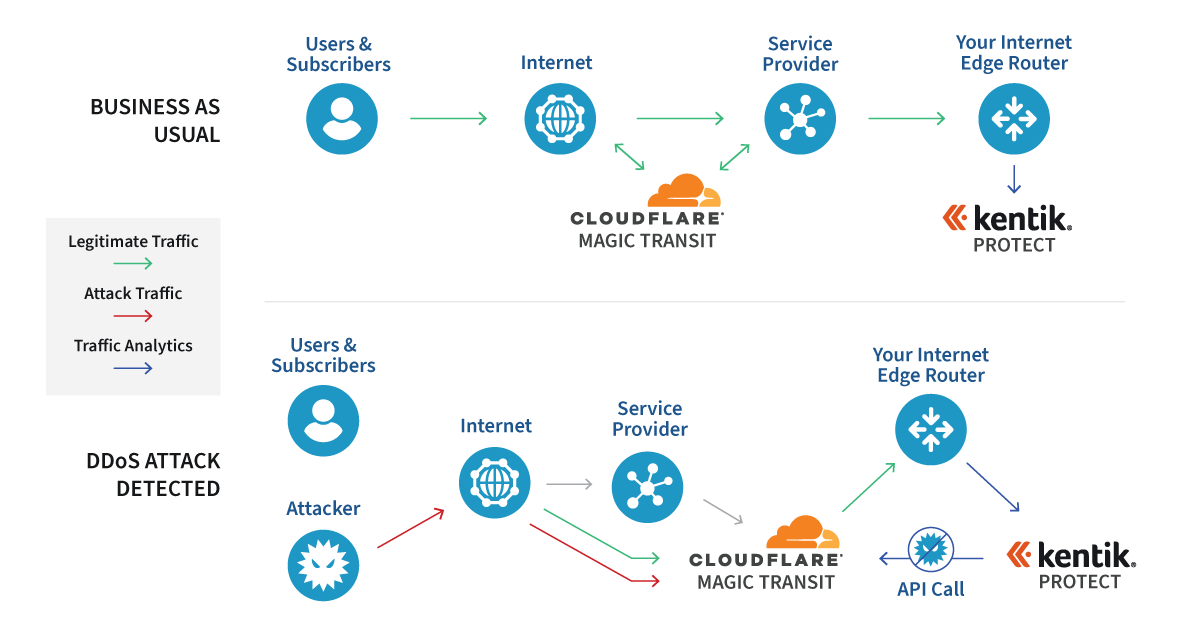
There are two primary means of detecting DDoS attacks: in-line examination of all packets and out-of-band detection via traffic flow record analysis. Either approach can be deployed on-premises or via cloud services.
Why am I seeing DDoS protection by Cloudflare?
If you see this “Checking your browser before accessing” message, Cloudflare is verifying the legitimacy of your browser and determining whether it is running any malicious scripts. Cloudflare is used to safeguard the website from hackers and to mitigate the effects of Distributed Denial-Of-Service attacks (DDoS).
How does Cloudflare detect DDoS?
To detect and mitigate DDoS attacks, Cloudflare’s Autonomous Edge and centralized DDoS systems analyze traffic samples “out-of-path”, which allows Cloudflare to asynchronously detect DDoS attacks without causing latency or impacting performance.
Are DDoS attacks illegal?
DDoSing is an Illegal cybercrime in the United States. A DDoS attack could be classified as a federal criminal offense under the Computer Fraud and Abuse Act (CFAA). The use of booter services and stressers also violates this act.
What are two examples of DoS attacks?
There are two general methods of DoS attacks: flooding services or crashing services. Flood attacks occur when the system receives too much traffic for the server to buffer, causing them to slow down and eventually stop. Popular flood attacks include: Buffer overflow attacks – the most common DoS attack.
Can you recover from a DDoS attack?
Your recovery depends on your provider’s and their set up. Once an attack ends, you should release your network once more. Often, ISP transit providers acknowledge your request almost immediately while peering partners could take longer.
How do hackers do DDoS attacks?
The primary way hackers accomplish DDoS attacks is through a network of remotely-controlled, hacked computers called botnets. These infected devices form what people know as “zombie networks” used to flood targeted websites, servers, and networks with more data than they can accommodate.
Why does Cloudflare keep checking my browser?
Cloudflare is just verifying that the request is made by a real browser and not by a malicious bot/script. Probably it will check some browser behaviour (like local storage, cookies etc) to verify its identity.
How do you detect a DDoS attack?
There are two primary means of detecting DDoS attacks: in-line examination of all packets and out-of-band detection via traffic flow record analysis. Either approach can be deployed on-premises or via cloud services.
Can anything be done to stop DDoS attacks?
More aggressively time out half-open connections whenever possible. Drop malformed and spoofed packages as early as possible. Rate limit your router to prevent volumetric DDoS attacks. Set lower thresholds for SYN, ICMP, and UDP flood.
What is a DDoS attack Cloudflare?
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
Can DDoS steal information?
1.5 – Can DDoS Attacks Steal Information? DDoS attacks cannot steal website visitors information. The sole purpose of a DDoS attack is to overload the website resources. However, DDoS attacks can be used as a way of extortion and blackmailing.
What does being Ddosed look like?
Symptoms of a DDoS attack can mimic issues you might find on your computer — slow access to website files, inability to access websites, or even problems with internet connection.
Is a DDoS a hack?
A DDoS attack isn’t the same thing as hacking, although the two can be linked; the perpetrators aren’t attempting to access your website’s files or admin, but instead, they cause it to crash or become vulnerable due to the volume of requests.
How much does it cost to DDoS a server?