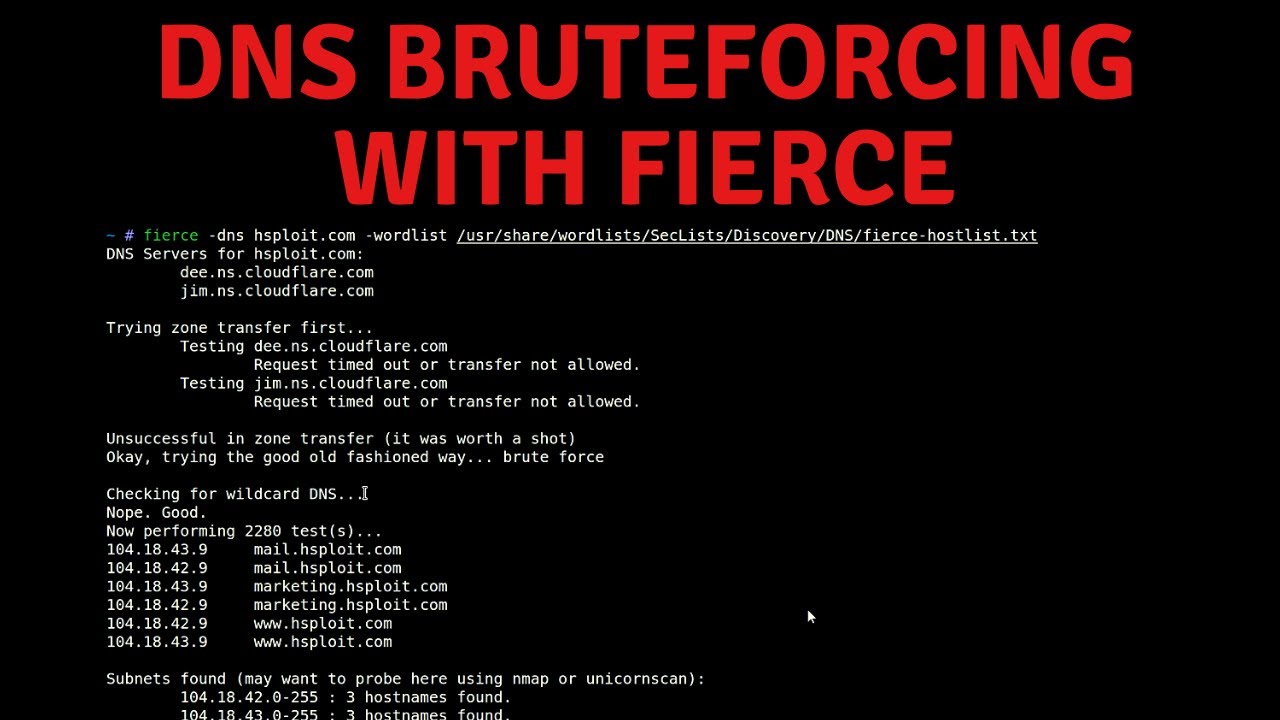
DNS Brute Force Attacks Brute force attacks use scripts or other tools to find all subdomains for a certain domain and expose the organization’s public—and possibly private—network. These attacks are usually precursors to more serious exploitation attempts.
What is subdomain brute-forcing?
Brute force means guessing possible combinations of the target until the expected output is discovered. So, in the subdomain context, the brute-forcing is to try the possible combination of words, alphabets, and numbers before the main domain in order to get a subdomain that is resolved to IP address.
What does DNS Recon do?
DNSRecon is a Python script that provides the ability to perform: Check all NS Records for Zone Transfers. Enumerate General DNS Records for a given Domain (MX, SOA, NS, A, AAAA, SPF and TXT). Perform common SRV Record Enumeration.
What is DNS brute?
Script dns-brute Attempts to enumerate DNS hostnames by brute force guessing of common subdomains. With the dns-brute. srv argument, dns-brute will also try to enumerate common DNS SRV records. Wildcard records are listed as “*A” and “*AAAA” for IPv4 and IPv6 respectively.
What is domain brute-forcing?
Brute-Forcing is the technique of matching the credentials like Usernames, Passwords, OTPs for unauthenticated access to the target domain. The list of words are been tested against the target to get the exact credentials. All this process is done through automated tools.
What is DNS brute?
Script dns-brute Attempts to enumerate DNS hostnames by brute force guessing of common subdomains. With the dns-brute. srv argument, dns-brute will also try to enumerate common DNS SRV records. Wildcard records are listed as “*A” and “*AAAA” for IPv4 and IPv6 respectively.
What is an example of brute force?
In their most straightforward form, brute force attacks seek to crack a password by exhausting all possible combinations through trial and error. For example, an attacker may attempt millions of combinations to guess a password.
What does a brute force do?
A brute force attack uses trial-and-error to guess login info, encryption keys, or find a hidden web page. Hackers work through all possible combinations hoping to guess correctly.
What happens if your DNS is attacked?
For example, DNS tunneling techniques enable threat actors to compromise network connectivity and gain remote access to a targeted server. Other forms of DNS attacks can enable threat actors to take down servers, steal data, lead users to fraudulent sites, and perform Distributed Denial of Service (DDoS) attacks.
Can DNS be attacked?
Like any other server, DNS servers are prone to all network-based attacks. There are many ways attackers can cause a large amount of network traffic to the DNS servers, such as TCP/UDP/ICMP floods, rendering the service unavailable to other network users by saturating the network link to the DNS servers.
Does Flushing DNS hurt anything?
Flushing DNS cache doesn’t greatly affect your internet speed. You’ll get rid of outdated cached data, but it might take a bit longer directly after the DNS cache flush to load different web pages, as the browser needs to re-fetch and re-cache the data.
Can brute force be traced?
If your web site requires user authentication, you are a good target for a brute-force attack. An attacker can always discover a password through a brute-force attack, but the downside is that it could take years to find it.
Do hackers still use brute force?
While some attackers still perform brute force attacks manually, today almost all brute force attacks today are performed by bots. Attackers have lists of commonly used credentials, or real user credentials, obtained via security breaches or the dark web.
What causes brute force?
Brute force attacks occur when a bad actor attempts a large amount of combinations on a target. These attacks frequently involve multiple attempts on account passwords with the hopes that one of them will be valid. It’s a bit like trying all of the possible combinations on a padlock, but on a much larger scale.
What are subdomain attacks?
Subdomain takeovers occur when an agent gains control over a subdomain of a target domain. This can happen when the subdomain has a canonical name in the DNS, but no host is providing content for it, which can happen because either a virtual host hasn’t been published yet or a virtual host has been removed.
What is subdomain in cyber security?
Security engineering usually refers to two key subdomains: network security and computer operations security. This domain is where your technical expertise is put to use in securing both the network and hosts from attacks. It’s in this domain that we lump the following: Firewalls. Router/switch security.
Why you should not use subdomain?
Using a subdomain on your website makes your URL structure look bigger. Subdomains are not regarded as ‘proper websites in the eyes of Google users. You will be responsible for more hosting fees as subdomains require separate hosting accounts. A subdomain may not yield your geolocation signal for search engines.
What is DNS brute?
Script dns-brute Attempts to enumerate DNS hostnames by brute force guessing of common subdomains. With the dns-brute. srv argument, dns-brute will also try to enumerate common DNS SRV records. Wildcard records are listed as “*A” and “*AAAA” for IPv4 and IPv6 respectively.
What are the two types of brute force attacks?
In a regular brute force attack, the attacker starts with a known key, usually a username or account number. Then they use automation tools to figure out the matching password. In a reverse brute force attack, the attacker knows the password and needs to find the username or account number.
What are brute force problems?
Brute forcing is generally accepted as the term for solving a problem in a roundabout, time-consuming, uncreative, and inconvenient method. Given the problem “How many outfits can you create with thirteen hats and seven pairs of shoes?”, a method involving brute force would be to list all 91 possibilities.
Where is brute force used?
Brute force attacks are usually used to obtain personal information such as passwords, passphrases, usernames and Personal Identification Numbers (PINS), and use a script, hacking application, or similar process to carry out a string of continuous attempts to get the information required.
How long do brute force attacks last?
Types of Brute Force Attacks Recent computers manufactured within the last 10ish years can brute force crack an 8 character alphanumeric password – capitals and lowercase letters, numbers, and special characters – in about two hours.