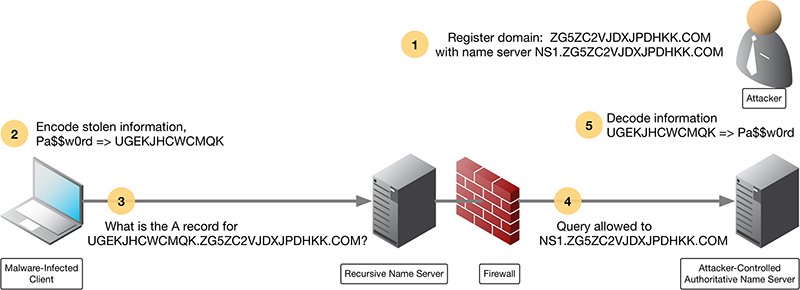
DNS data exfiltration is a way to exchange data between two computers without any direct connection. The data is exchanged through DNS protocol on intermediate DNS servers. During the exfiltration phase, the client makes a DNS resolution request to an external DNS server address.
Why was DNS selected as the means to exfiltrate data?
DNS is frequently used as a pathway for data exfiltration, because it is not inspected by common security controls.
What causes data exfiltration?
Besides users with malicious intentions, accidental insider threats can be a major cause of data exfiltration. Phishing emails and social engineering attacks remain a tried-and-true way for hackers to access company data.
How do attackers use the DNS process to stage commands and exfiltrate data?
The attacker uses a host they have infected with malware to query for the attacker-controlled domain. When the DNS resolver routes the query, it creates a tunnel from the attacker to their target, allowing them to get data, remotely control the host, or otherwise take the next step in the attack chain.
How does DNS tunnel work?
DNS tunneling exploits the DNS protocol to tunnel malware and other data through a client-server model. The attacker registers a domain, such as badsite.com. The domain’s name server points to the attacker’s server, where a tunneling malware program is installed.
What is DNS tunneling?
DNS tunneling involves abuse of the underlying DNS protocol. Instead of using DNS requests and replies to perform legitimate IP address lookups, malware uses it to implement a command and control channel with its handler. DNS’s flexibility makes it a good choice for data exfiltration; however, it has its limits.
What is exfiltration detection?
Data exfiltration is a technique used by malicious actors to target, copy, and transfer sensitive data. Data exfiltration can be done remotely or manually and can be extremely difficult to detect given it often resembles business-justified (or “normal”) network traffic.
How do hackers exfiltrate data?
They could exfiltrate data either through physical vectors, like flash drives, or digital vectors, by diverting network traffic to cloud storage services. External Threats – Cybercriminals prefer external data exfiltration methods because these attacks can be launched remotely from anywhere in the world.
How is data exfiltration detected?
One of the methods used in detecting data exfiltration should be the monitoring of the e-mails, DNS inquiries, file access demands, and illegal port connections. Detection is made easier when monitoring panels and alerts are formed. Logsign SIEM detects the abnormal behavior of the user by means of a correlation motor.
How DNS can be attacked?
The attacker corrupts a DNS server by replacing a legitimate IP address in the server’s cache with that of a rogue address to redirect traffic to a malicious website, collect information or initiate another attack. Cache poisoning are also referred to as DNS poisoning.
What are two types of attacks used on DNS open?
DNS Open-resolvers are also vulnerable to Cache Poisoning and can be exploited in other types of DNS attacks, such as DNS tunneling, DNS hijack attack, NXDOMAIN attack, Random subdomain attack and Phantom domain attack.
How can data exfiltration be prevented?
To reduce the risk of data exfiltration, organizations must integrate security awareness and best practices into their culture. They must consistently evaluate the risks of every interaction with computer networks, devices, applications, data, and other users.
How do I check my DNS exfiltration?
DNS tunneling poses a significant threat and there are methods to detect it. DNS tunnels can be detected by analyzing a single DNS payload or by traffic analysis such as analyzing count and frequency of requests. Payload analysis is used to detect malicious activity based on a single request.
How do I protect DNS tunneling?
Protection against DNS Tunneling attacks You can set all of the internal clients to direct their DNS requests (DNS queries) to an internal DNS server. That way, you can filter potential malicious domains.
How do I stop DNS tunneling?
Preventive measures for DNS Tunneling To avoid the possession of data, a tool must be installed that blacklists the destinations which are to extract data. This activity must be done on a regular basis. A DNS firewall should be configured and designed such that it quickly identifies any intrusion.
How are domains hijacked?
How are Domains Hijacked? Domain hijacking occurs from illegal access to or exploitation of a common cybersecurity vulnerability in a domain name registrar, or from acquiring access to the domain name owner’s email address and then changing the password to the owner’s domain name registrar.
What is DNS trafficking?
What is a DNS hijacking / redirection attack. Domain Name Server (DNS) hijacking, also named DNS redirection, is a type of DNS attack in which DNS queries are incorrectly resolved in order to unexpectedly redirect users to malicious sites.
Is exfiltration data illegal?
Many data leaks are the result of data exfiltration or the illegal transfer of data from a device containing sensitive information to unauthorized parties.
What is the purpose of an exfiltration trench?
Some exfiltration trenches are designed to retain all stormwater from a drainage basin with no outflow other than recharge; others are designed to detain the first inch of stormwater before overflow begins by means of a discharge pipe.
Which of the following is an example of data exfiltration?
Types of exfiltrated data Usernames, associated passwords, and other system authentication related information. Information associated with strategic decisions. Cryptographic keys. Personal financial information.
What does ransomware do?
Ransomware is a malware designed to deny a user or organization access to files on their computer. By encrypting these files and demanding a ransom payment for the decryption key, cyberattackers place organizations in a position where paying the ransom is the easiest and cheapest way to regain access to their files.
Which of the following service is used in the data exfiltration process in the cloud watch?
Answer. AWS CloudTrail along with AWS Lambda is the service use to detect Data Exfiltration.