A good practice is to use a Web Application Firewall (WAF) against attacks, such as SQL injection or cross-site request forgery, that attempt to exploit a vulnerability in your application itself.
Which of the following can be used to protect against DDoS attacks AWS?
AWS Shield Standard and AWS Shield Advanced provide protections against Distributed Denial of Service (DDoS) attacks for AWS resources at the network and transport layers (layer 3 and 4) and the application layer (layer 7).
Is there a way to stop a DDoS attack?
Attack Tolerance and Mitigation Typical steps to counter DDoS attacks include, but are not limited to: Rate Limiting: Block users that exceed a threshold for requests. Source Blocking: Block IP addresses known to be attacking. Traffic Rerouting: Move the application or device to a new IP and reroute legitimate traffic.
How does DDoS protection work?
DDoS mitigation providers filter out malicious traffic to prevent it from reaching the intended targeted asset. Attack traffic is blocked by a DDoS scrubbing service, a cloud-based DNS service, or a CDN-based web protection service. Cloud-based mitigation removes attack traffic before it reaches the target.
Can firewall prevent DDoS?
Firewalls Can’t Protect You from DDoS Attacks. Although firewalls are designed to, and still do, protect networks from a variety of security issues, there are gaping holes when it comes to DDoS and malicious server targeted attacks.
What is DDoS attack mean?
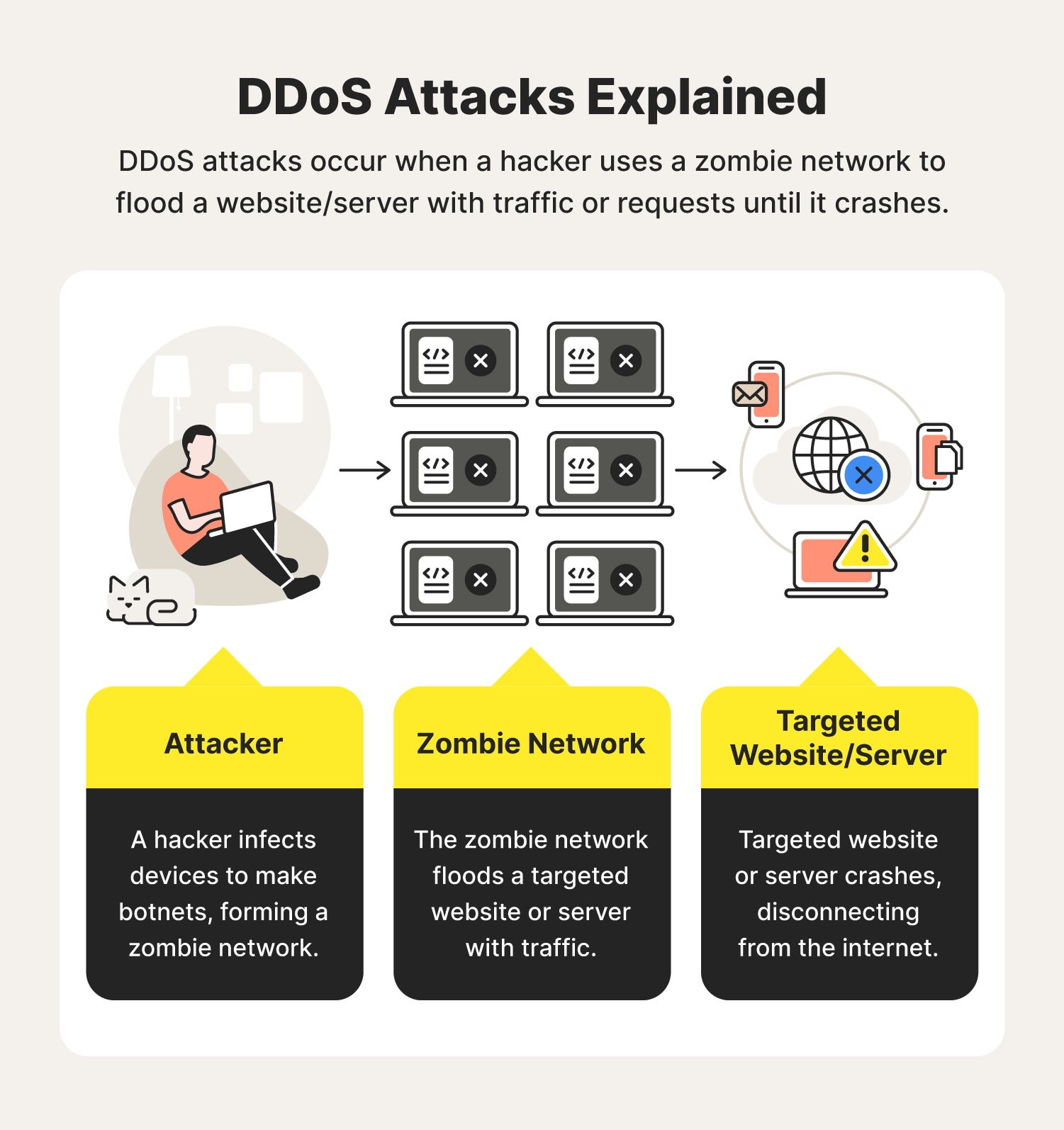
Distributed denial of service (DDoS) attacks are a subclass of denial of service (DoS) attacks. A DDoS attack involves multiple connected online devices, collectively known as a botnet, which are used to overwhelm a target website with fake traffic.
Does AWS WAF protect against DDoS?
For infrastructure layer attacks, you can use AWS services such as Amazon CloudFront and Elastic Load Balancing (ELB) to provide automatic DDoS protection. For more information, see AWS best practices for DDoS resiliency. For application layer attacks, you can use AWS WAF as the primary mitigation.
Does AWS CloudFront protect against DDoS?
AWS Shield, a DDoS protection service, is enabled by default on Amazon CloudFront and automatically protects against Network/Transport layer DDoS attacks.
How does AWS Shield prevent DDoS?
Static threshold DDoS protection for underlying AWS services AWS Shield Standard provides always-on network flow monitoring, which inspects incoming traffic to AWS services and applies a combination of traffic signatures, anomaly algorithms, and other analysis techniques to detect malicious traffic in real time.
How do hackers do DDoS attacks?
In a DDoS attack, cybercriminals take advantage of normal behavior that occurs between network devices and servers, often targeting the networking devices that establish a connection to the internet. Therefore, attackers focus on the edge network devices (e.g., routers, switches), rather than individual servers.
How do you DDoS someone?
A DDoS attack is a type of cyberthreat based on sending too many requests to an online resource, forcing that site or resource offline. The attacker takes advantage of a vast network of computers to create this pressure, often by using “zombie” machines they have taken over through malware.
What is anti DDoS protection?
Anti-DDoS hardware is a physical layer of protection between potential attackers and your network. Although anti-DDoS hardware can protect from certain types of attacks – other types, like DNS attacks, are not influenced at all by hardware, as the damage is done before traffic even reaches the device.
Why DDoS protection is required?
Distributed denial of service (DDoS) attacks are some of the largest availability and security concerns facing customers that are moving their applications to the cloud. A DDoS attack attempts to exhaust an application’s resources, making the application unavailable to legitimate users.
What is DDoS in cyber security?
DDoS (Distributed Denial of Service) is a category of malicious cyber-attacks that hackers or cybercriminals employ in order to make an online service, network resource or host machine unavailable to its intended users on the Internet.
How do servers protect against DDoS?
DDoS Protection Techniques In some cases, you can do this by placing your computation resources behind Content Distribution Networks (CDNs) or Load Balancers and restricting direct Internet traffic to certain parts of your infrastructure like your database servers.
Which of the following can stop attacks on the network?
A firewall system will block any brute force attacks made on your network and/or systems before it can do any damage, something we can help you with.
What is DDoS protection by Cloudflare?
Cloudflare DDoS protection secures websites, applications, and entire networks while ensuring the performance of legitimate traffic is not compromised. Cloudflare’s 155 Tbps network blocks an average of 124 billion threats per day, including some of the largest DDoS attacks in history.
What is a DDoS attack and how is it mitigated?
Distributed denial of service attack (DDoS) definition A distributed denial of service (DDoS) attack is a malicious attempt to make an online service unavailable to users, usually by temporarily interrupting or suspending the services of its hosting server.
Which of the following is a form of DoS attack?
There are two general methods of DoS attacks: flooding services or crashing services. Flood attacks occur when the system receives too much traffic for the server to buffer, causing them to slow down and eventually stop. Popular flood attacks include: Buffer overflow attacks – the most common DoS attack.
Why do DDoS attacks?
Usually, the attacker’s ultimate aim is the total prevention of the web resource’s normal functioning – a total ‘denial of service’. The attacker may also request payment for stopping the attack. In some cases, a DDoS attack may even be an attempt to discredit or damage a competitor’s business.
What is the largest DOS or DDoS?
The record-breaking 3.47 Tbps DDoS attack originated from approximately 10,000 sources from connected devices in the United States, China, South Korea, Russia, Thailand, India, Vietnam, Iran, Indonesia, and Taiwan. “We believe this to be the largest attack ever reported in history,” said Toh.
How long are DDoS attacks?