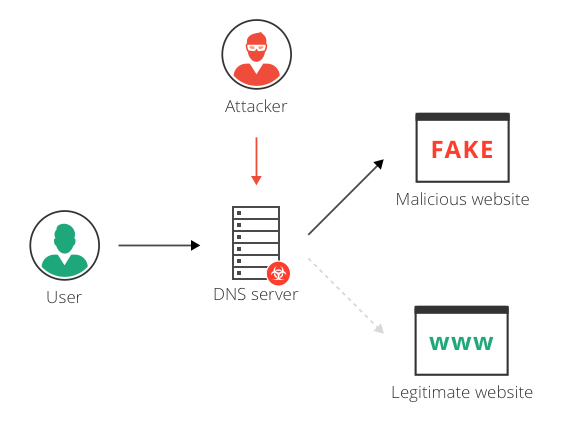
DNS hijacking can be used for pharming (in this context, attackers typically display unwanted ads to generate revenue) or for phishing (displaying fake versions of sites users access and stealing data or credentials).
Why do hackers spoof DNS?
Domain name system (DNS) spoofing is a type of cyberattack that uses tampered DNS server data to redirect users to fake websites. These malicious sites often look legitimate but are actually designed to install malware onto users’ devices, steal sensitive data or redirect traffic.
Why do people attack DNS?
DNS attacks are any type of attack that involves the domain name system (DNS). There are many different ways that attackers can take advantage of weaknesses in the DNS. Most of these attacks are focused on abusing the DNS to stop internet users from being able to access certain websites.
What can someone do with my DNS?
A local DNS attack installs malware on the website user’s computer. The malware, usually a trojan malware disguised as legitimate software, gives the cyber thieves access to users’ network systems, enabling them to steal data and change DNS settings to direct the users to malicious websites.
What happens when DNS hacked?
In a DNS server hack, your query is redirected in the wrong destination by a DNS server under a hacker’s control. This attack is even more cunning because once the query leaves your device, you have no control whatsoever over the direction your traffic takes.
What can someone do with my DNS?
A local DNS attack installs malware on the website user’s computer. The malware, usually a trojan malware disguised as legitimate software, gives the cyber thieves access to users’ network systems, enabling them to steal data and change DNS settings to direct the users to malicious websites.
Can hackers change your DNS?
DNS servers are a vital part of internet infrastructure, but they can be manipulated by hackers to redirect you to corrupted websites or steal your private data. Here’s how to configure your router DNS settings to prevent hijacking attacks.
What is a DNS attack?
A Domain Name System (DNS) attack is one in which a bad actor either tries to compromise a network’s DNS or takes advantage of its inherent attributes to conduct a broader attack. A well-orchestrated DNS attack can bring an organization to its knees.
Can you be tracked through DNS?
Tracking and Logging DNS Requests DNS monitoring can also discover and track IP addresses of DNS requests and log every website viewed by a device connected to your network. This helps your network team find out which websites your employees are visiting and how long it takes to complete the DNS request.
Can a DNS server track you?
They can glean a lot of information about your browsing habits this way. Changing DNS servers won’t stop your ISP from tracking, but it will make it a little harder. Using a virtual private network (VPN) for your daily browsing is the only real way to prevent your ISP from seeing what you’re connecting to online.
Is DNS hijacking common?
DNS hijacking is a common cyberattack technique known as domain name server reconfiguration.
How do you know if my DNS has been hacked?
You’re Redirected to Unintended or Unknown Websites If you’re trying to visit your regular round of websites and you keep getting redirected to websites you weren’t intending to visit, then this could be a sign of a hacked router using DNS hijacking.
How DNS can be attacked?
The attacker corrupts a DNS server by replacing a legitimate IP address in the server’s cache with that of a rogue address to redirect traffic to a malicious website, collect information or initiate another attack. Cache poisoning are also referred to as DNS poisoning.
Is DNS a security risk?
DNS attacks are among the most prevalent and effective web security threats.
Why is DNS spoofing a problem?
They both trick users into divulging sensitive data, and they both could result in a targeted user installing malicious software. Both DNS spoofing and poisoning pose a risk to user data privacy and the security of a website connection as users communicate with servers on a public Wi-Fi.
How hackers exploit the vulnerabilities in the DNS?
Yet DNS, like any other protocol on the internet, can be manipulated and exploited. A malicious attacker can take advantage of the domain name resolution by attacking the DNS server and changing its records to return incorrect information about domain names or websites instead of their correct IP addresses.
How common is DNS spoofing?
Through their research they discovered that DNS spoofing is still rare (occurring only in about 1.7% of observations) but has been increasing during the observed period, and that proxying is the most common DNS spoofing mechanism.
What can someone do with my DNS?
A local DNS attack installs malware on the website user’s computer. The malware, usually a trojan malware disguised as legitimate software, gives the cyber thieves access to users’ network systems, enabling them to steal data and change DNS settings to direct the users to malicious websites.
What happens when DNS hacked?
In a DNS server hack, your query is redirected in the wrong destination by a DNS server under a hacker’s control. This attack is even more cunning because once the query leaves your device, you have no control whatsoever over the direction your traffic takes.
How do hackers exploit DNS?
Attackers can take over a router and overwrite DNS settings, affecting all users connected to that router. Man in the middle DNS attacks — attackers intercept communication between a user and a DNS server, and provide different destination IP addresses pointing to malicious sites.
How could DNS be abused by attackers?
DNS Cache Poisoning Attacks introducing data into a DNS resolver’s cache, causing the name server to return an incorrect IP address for further requests, diverting traffic to the attacker’s computer.
What is a DNS vulnerability?
A DNS Exploit is a vulnerability in the domain name system (DNS) through which an attacker an infiltrate a network.