Most of the time, DNS spoofing or cache poisoning just involves overwriting your local DNS cache values with fake ones so you can be redirected to a malicious website. On the other hand, DNS hijacking (also known as DNS redirection) often involves malware infections in order to hijack this important system service.
What is DNS poisoning?
DNS poisoning is a hacker technique that manipulates known vulnerabilities within the domain name system (DNS). When it’s completed, a hacker can reroute traffic from one site to a fake version. And the contagion can spread due to the way the DNS works.
What is DNS server hijacking?
Domain Name Server (DNS) hijacking, also named DNS redirection, is a type of DNS attack in which DNS queries are incorrectly resolved in order to unexpectedly redirect users to malicious sites.
What is the difference between DNS poisoning and ARP poisoning?
While DNS poisoning spoofs IP addresses of legitimate sites and its effect can spread across multiple networks and servers, ARP poisoning spoofs physical addresses (MAC addresses) within the same network segment (subnet).
What is another name for DNS poisoning?
DNS cache poisoning is the act of entering false information into a DNS cache, so that DNS queries return an incorrect response and users are directed to the wrong websites. DNS cache poisoning is also known as ‘DNS spoofing.
What is DNS server hijacking?
Domain Name Server (DNS) hijacking, also named DNS redirection, is a type of DNS attack in which DNS queries are incorrectly resolved in order to unexpectedly redirect users to malicious sites.
How is DNS poisoning done?
DNS cache poisoning is a user-end method of DNS spoofing, in which your system logs the fraudulent IP address in your local memory cache. This leads the DNS to recall the bad site specifically for you, even if the issue gets resolved or never existed on the server-end.
Why do hackers use DNS poisoning?
DNS poisoning is a spoofing activity in which hackers redirect original traffic to a fraudulent website. DNS poisoning makes it easy to access sensitive information on a device or in the interrupted web traffic flow.
How many types of DNS hijacking are there?
Types of DNS Hijacking Attacks Cybercriminals can achieve DNS hijacking through four different ways: Local DNS Hijack: This DNS hijacking method is achieved when a cybercriminal installs a Trojan malware on a website user’s computer.
What does hijacking mean in networking?
Cyber hijacking, or computer hijacking, is a type of network security attack in which the attacker takes control of computer systems, software programs and/or network communications.
What is the main difference between DNS and ARP?
What is the main difference between DNS and ARP? DNS resolves host names for hosts anywhere online while ARP only resolves IP addresses of hosts and router interfaces within the same subnet.
Which of the following is an example of DNS poisoning?
DNS poisoning can ultimately route users to the wrong website. For example, a user may enter “msn.com” into a web browser, but a page chosen by the attacker loads instead. Since users are typing in the correct domain name, they may not realize that the website they are visiting is fake.
What is difference between spoofing and poisoning?
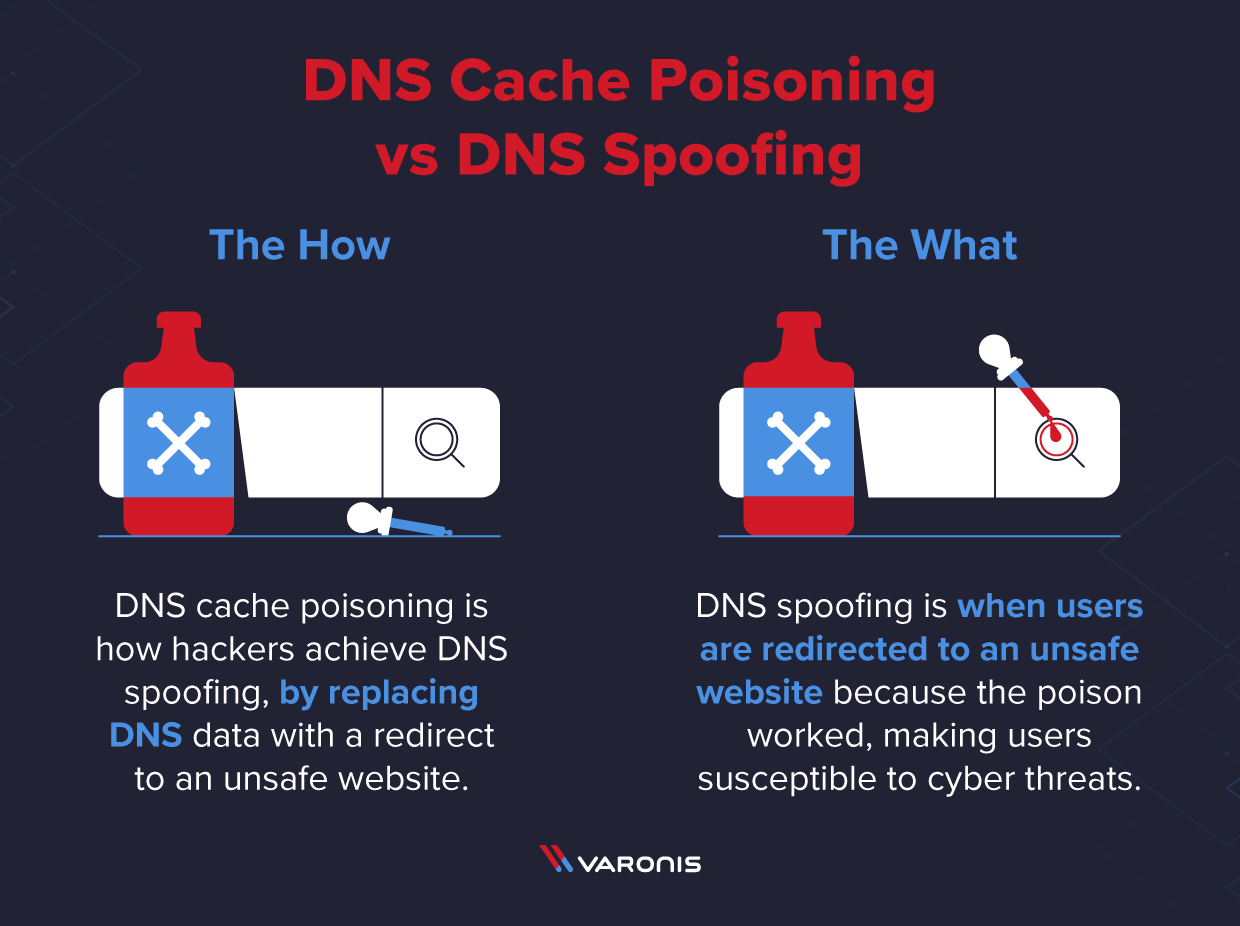
While the terms DNS poisoning and DNS spoofing are used interchangeably, there’s a difference between the two. DNS Poisoning is the method attackers use to compromise and replace DNS data with a malicious redirect. DNS Spoofing is the end result, where users are redirected to the malicious website via a poisoned cache.
What are 3 types of DNS records?
The three DNS server types server are the following: DNS stub resolver server. DNS recursive resolver server. DNS authoritative server.
How do I know if my DNS is poisoned?
A sudden increase in DNS activity from a single source about a single domain indicates a potential Birthday attack. An increase in DNS activity from a single source that is querying your DNS server for multiple domain names without recursion indicates an attempt to find an entry to use for poisoning.
What problems can DNS cause?
If DNS isn’t working properly, you won’t be able to use web-connected services, such as your browser or email, despite your computer or router showing a working internet connection. The webpage may timeout, give you an error message, or even bring up a specific “DNS error” message.
What happens if your DNS is attacked?
For example, DNS tunneling techniques enable threat actors to compromise network connectivity and gain remote access to a targeted server. Other forms of DNS attacks can enable threat actors to take down servers, steal data, lead users to fraudulent sites, and perform Distributed Denial of Service (DDoS) attacks.
What happens if your DNS is leaked?
What Does a DNS Leak Mean in Terms of Privacy and Security? So, a DNS leak means that someone can intercept the communications between your browser and DNS or steal the data from a DNS cache even though you’re using a virtual private network (VPN). This is also known as an IP leak.
What is DNS server hijacking?
Domain Name Server (DNS) hijacking, also named DNS redirection, is a type of DNS attack in which DNS queries are incorrectly resolved in order to unexpectedly redirect users to malicious sites.
Which can be used to prevent DNS poisoning?
Use VPN: These services provide an encrypted tunnel for all web traffic. It also provides the end-to-end encrypted security that a private DNS server requires. As a consequence, it gives us requests that cannot be obstructed and servers that are much more resistant to DNS spoofing.
How do I know if my DNS is poisoned?
A sudden increase in DNS activity from a single source about a single domain indicates a potential Birthday attack. An increase in DNS activity from a single source that is querying your DNS server for multiple domain names without recursion indicates an attempt to find an entry to use for poisoning.
What is an example of hijacking?
Example Sentences He hijacked a truck, threatening the driver at gunpoint. A band of robbers hijacked the load of furs from the truck. A group of terrorists hijacked the plane. The organization has been hijacked by radicals.