Iphone
-

 476
476How do you force an unresponsive iPhone to restart?
Press and release the volume-up button. Press and release the volume-down button. Press and hold the side button until the screen turns...
-

 444
444How do I shutdown my MacBook Air with keyboard?
Control–Option–CommandCommandThe Command key (sometimes abbreviated as Cmd key), ⌘, formerly also known as the Apple key or open Apple key, is a...
-
 433
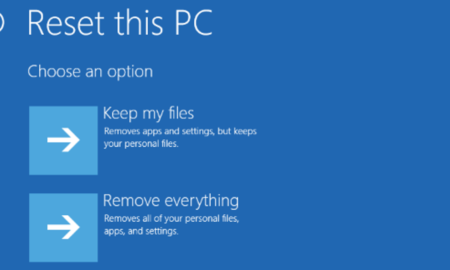
433How often should I reset PC?
If your computer is starting to get sluggish or have issues, then it’s past time to do a reboot. According to the...
-
 423
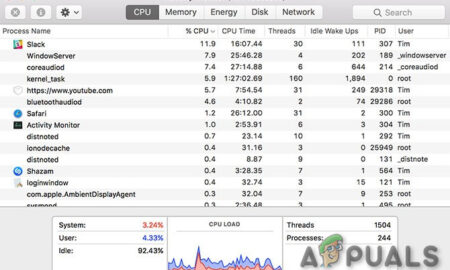
423Why is kernel_task running on my Mac?
The primary function of the (kernel task) process is to regulate the temperature of your Mac’s CPU. Every time you power on...
-
 645
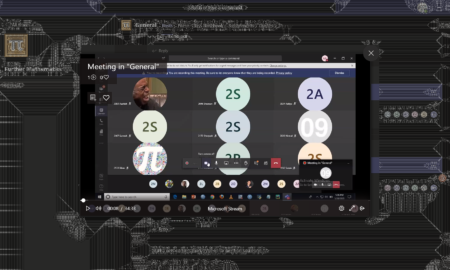
645What does white circle on Teams mean?
Once set, offline status is shown as a white circle with a grey edge (Figure 2). It’s the same visual indicator shown...
-
 591
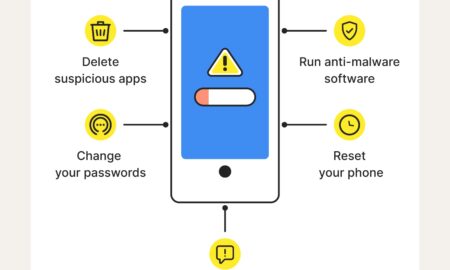
591Can you tell if your phone is hacked?
Use the code *#21# to see if hackers track your phone with malicious intent. You can also use this code to verify...
-

 520
520Can someone track my phone by texting me?
With their GPS radios and constant data connection, smartphones are technically capable of tracking our location and monitoring our activity, which is...
-

 499
499Can you Unhack your phone?
If you’ve recently sideloaded apps on Android, they might be to blame for the hack. Therefore, to unhack your phone, delete all...
-

 561
561How far away can a listening device work?
How Far Away Can Listening Devices Hear a Conversation? Some of these devices can allow someone to hear a conversation from 100...
-

 556
556Can someone see you through your phone without you knowing it?
Even if you’re cautious about what information you reveal online, it’s possible someone could stalk you via apps installed on your smartphone....

Recent Comments