Latest News
-
 406Linux
406LinuxWhy is DNS over HTTPS controversial?
DNS over HTTPS is a controversial internet privacy technology which would encrypt DNS connections and hide them in the common HTTPS traffic,...
-
 570Rainbow
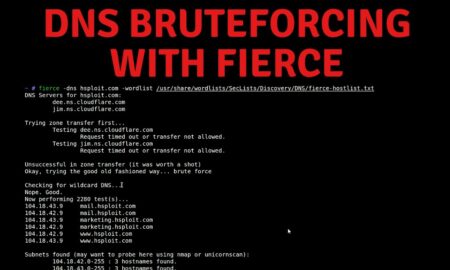
570RainbowWhat is a DNS brute force?
DNS Brute Force Attacks Brute force attacks use scripts or other tools to find all subdomains for a certain domain and expose...
-
 461Adobe
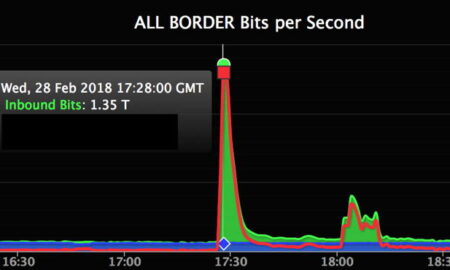
461AdobeWhich one is a very famous DNS attack?
One of the largest verifiable DDoS attacks on record targeted GitHub, a popular online code management service used by millions of developers....
-
 517Need
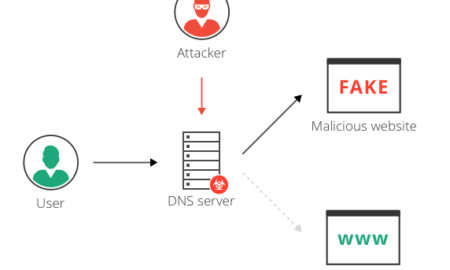
517NeedHow do hackers redirect traffic?
Local DNS hijack — attackers install Trojan malware on a user’s computer, and change the local DNS settings to redirect the user...
-

 419Startup
419StartupWhat is the difference between DNS poisoning and DNS hijacking?
Most of the time, DNS spoofing or cache poisoning just involves overwriting your local DNS cache values with fake ones so you...
-
 426Android
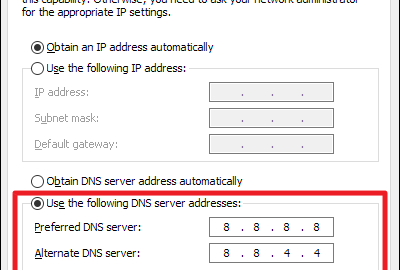
426AndroidDoes Google DNS make WIFI faster?
Google and OpenDNS attach your IP address to the DNS requests. This means that the data is loaded from a server local...
-
 429Fashion
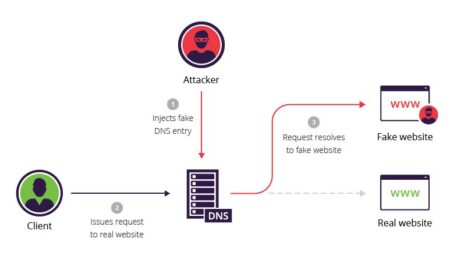
429FashionWhat is DNS poisoning explain with one example?
DNS Poisoning (DNS Spoofing): Definition, Technique & Defense. During a DNS poisoning attack, a hacker substitutes the address for a valid website...
-
 447Mobile
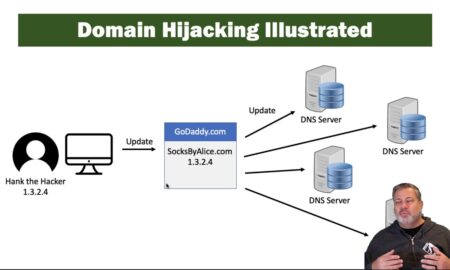
447MobileHow are domains hijacked?
How Does Domain Hijacking Work? Generally domain hijacking occurs from unauthorized access to, or exploitation of a vulnerability in a domain name...
-
 456Info
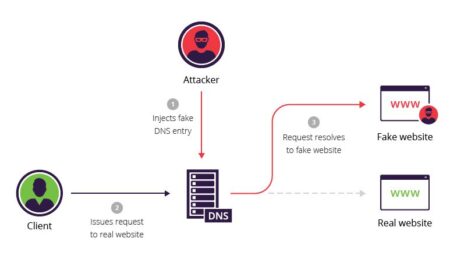
456InfoWhat is example of DNS poisoning?
What is another name for DNS poisoning? DNS cache poisoning is the act of entering false information into a DNS cache, so...
-

 397Reboot
397RebootWhat is exploit the DNS system?
A DNS Exploit is a vulnerability in the domain name system (DNS) through which an attacker an infiltrate a network. What do...
