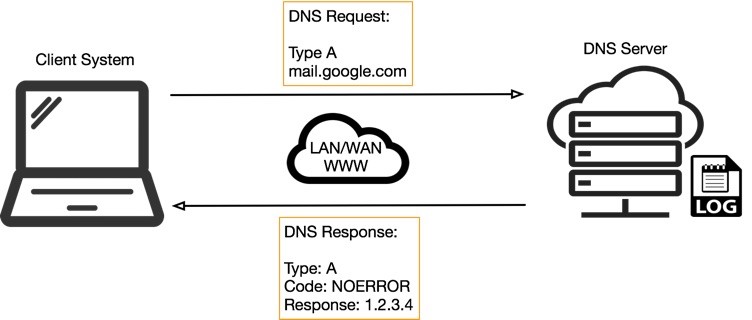
Yet DNS, like any other protocol on the internet, can be manipulated and exploited. A malicious attacker can take advantage of the domain name resolution by attacking the DNS server and changing its records to return incorrect information about domain names or websites instead of their correct IP addresses.
How DNS can be attacked?
The attacker corrupts a DNS server by replacing a legitimate IP address in the server’s cache with that of a rogue address to redirect traffic to a malicious website, collect information or initiate another attack. Cache poisoning are also referred to as DNS poisoning.
How do hackers attack DNS?
DNS servers, routers and computers cache DNS records. Attackers can “poison” the DNS cache by inserting a forged DNS entry, containing an alternative IP destination for the same domain name. The DNS server resolves the domain to the spoofed website, until the cache is refreshed.
What are the threats to DNS server?
Network Floods Like any other server, DNS servers are prone to all network-based attacks. There are many ways attackers can cause a large amount of network traffic to the DNS servers, such as TCP/UDP/ICMP floods, rendering the service unavailable to other network users by saturating the network link to the DNS servers.
What is exploit the DNS system?
Why would an attacker want to hijack DNS service?
Display ads to generate revenue Attackers can hijack your DNS to display unwanted ads to generate revenue, in a technique known as pharming. In a less fraudulent sense, your internet service provider can also manipulate your DNS requests to show ads to you.
Can private DNS be hacked?
DNS servers are a vital part of internet infrastructure, but they can be manipulated by hackers to redirect you to corrupted websites or steal your private data.
Can Google DNS be hacked?
Hackers create malware programs that can change your DNS server settings. For example, if your computer uses Google’s DNS servers and you want to go to your bank’s website, you type in the URL of your bank and expect to be taken to your bank’s official website.
Which one is a very famous DNS attack?
What is an example of DNS spoofing?
What is example of DNS poisoning?
DNS poisoning can ultimately route users to the wrong website. For example, a user may enter “msn.com” into a web browser, but a page chosen by the attacker loads instead. Since users are typing in the correct domain name, they may not realize that the website they are visiting is fake.
How are domains hijacked?
A true hijack of a domain happens when a domain’s legitimate owner unwittingly loses it. This occurs when they volunteer their Domain Name System (DNS) credentials as a result of a phishing or other social engineering scam.
How do I know if my DNS is poisoned?
The main symptom of a DNS poisoning attack is a sudden, unexplained drop in web traffic. Though web traffic is always volatile, if you see a sudden reduction in the number of visitors to your site, it’s always worth investigating why.
What is a DNS virus?
By controlling DNS, a criminal can get an unsuspecting user to connect to a fraudulent website or to interfere with that user’s online web browsing. One way criminals do this is by infecting computers with a class of malicious software (malware) called DNSChanger.
What is example of DNS poisoning?
DNS poisoning can ultimately route users to the wrong website. For example, a user may enter “msn.com” into a web browser, but a page chosen by the attacker loads instead. Since users are typing in the correct domain name, they may not realize that the website they are visiting is fake.
How are domains hijacked?
A true hijack of a domain happens when a domain’s legitimate owner unwittingly loses it. This occurs when they volunteer their Domain Name System (DNS) credentials as a result of a phishing or other social engineering scam.
What is DNS poisoning explain with one example?
Is DNS secure?
DNS is widely trusted by organizations, and DNS traffic is typically allowed to pass freely through network firewalls. However, it is commonly attacked and abused by cybercriminals. As a result, the security of DNS is a critical component of network security.
What are two methods used by cybercriminals to mask DNS attacks?
What are two methods used by cybercriminals to mask DNS attacks? (Choose two.) Answers Explanation & Hints: Fast flux, double IP flux, and domain generation algorithms are used by cybercrimals to attack DNS servers and affect DNS services.
What is the difference between DNS poisoning and DNS hijacking?
Domain Name System (DNS) poisoning, sometimes referred to as DNS hijacking, redirection, spoofing, or cache poisoning, is a type of cyberattack where traffic is maliciously diverted from a legitimate site to a fake site.
How do hackers redirect traffic?
Man-in-the-middle DNS Hijack: This is done by hackers operating within the communication between a network user and a DNS server to obstruct such communication and eventually redirect the user to an unknown destination IP address leading to harmful websites. It is also referred to as DNS spoofing.
What is a DNS brute force?
DNS brute force attack is a method to gather all subdomains of a particular domain by using scripts or other tools and sending legitimately looking queries.